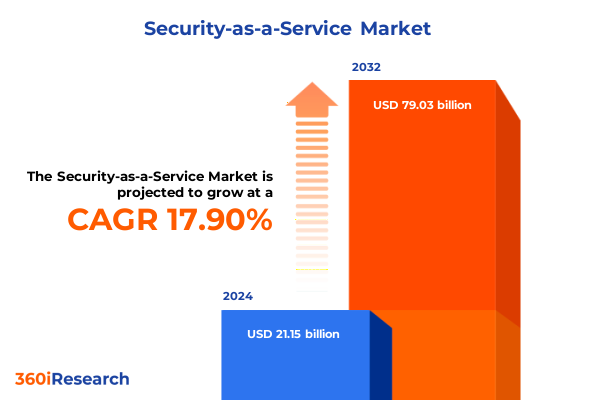
The Security-as-a-Service Market size was estimated at USD 24.88 billion in 2025 and expected to reach USD 29.14 billion in 2026, at a CAGR of 17.95% to reach USD 79.03 billion by 2032.
Understanding the Strategic Imperative and Core Benefits Driving the Adoption of Security-as-a-Service in Today’s Enterprise Ecosystems
Organizations today face an unprecedented convergence of evolving cyberthreats, complex regulatory landscapes, and accelerated digital transformation initiatives. In this context, Security-as-a-Service emerges as a strategic imperative, offering on-demand access to advanced protection capabilities that would otherwise require substantial capital investment and in-house expertise. By leveraging cloud-native architectures and subscription-based models, enterprises can achieve continuous security improvements while maintaining the agility to respond swiftly to new risks.
Moreover, the consumption-oriented framework of Security-as-a-Service enables organizations to align security spending with actual usage, facilitating budget predictability and operational efficiency. This approach is particularly beneficial for businesses adopting multi-cloud and hybrid environments, as it provides consistent policy enforcement and visibility across disparate networks. As a result, security teams can focus their resources on threat analysis and incident response, rather than managing hardware appliances or software licenses.
Furthermore, the scalability and flexibility inherent in Security-as-a-Service support rapid deployment of new capabilities, such as advanced threat intelligence, behavioral analytics, and automated incident response workflows. This dynamic adaptability ensures that security postures remain resilient amidst shifting threat landscapes, emerging compliance mandates, and fluctuating business priorities. Consequently, Security-as-a-Service not only addresses current security challenges but also establishes a robust foundation for sustained, proactive risk management.
Exploring the Transformative Technological and Operational Shifts Reshaping the Security-as-a-Service Market for Modern Organizations
The Security-as-a-Service market is undergoing transformative shifts driven by technological innovation, evolving threat tactics, and changing workforce dynamics. One of the most significant transformations is the migration from perimeter-centric defenses toward distributed, zero-trust architectures. By continuously validating every user, device, and application request, zero-trust principles enhance visibility and reduce the attack surface, effectively countering sophisticated intrusion techniques such as credential theft and lateral movement.
In parallel, the integration of artificial intelligence and machine learning into Security-as-a-Service platforms has revolutionized threat detection and response. These capabilities enable real-time analysis of massive data streams, facilitating early identification of anomalous activity and automated remediation workflows. Consequently, security operations centers can operate more efficiently and with greater precision, minimizing dwell time and limiting potential damage from breaches.
Simultaneously, the rise of remote and hybrid work models has amplified the importance of cloud-based security controls. As employees access corporate resources from diverse locations and devices, Security-as-a-Service offerings provide a unified framework for enforcing consistent policies, protecting sensitive data, and securing endpoints. These combined shifts are reshaping vendor strategies, driving consolidation of point solutions, and fostering partnerships across cloud providers to deliver integrated, adaptable security ecosystems.
Assessing the Far-Reaching Cumulative Impact of United States 2025 Tariff Policies on Security-as-a-Service Supply Chains and Costs
United States tariff measures instituted in early 2025 have introduced new variables affecting the cost dynamics and supply chain structures within the Security-as-a-Service ecosystem. Specifically, higher duties on imported hardware components and network infrastructure have elevated procurement costs for on-premise appliances and edge computing devices, prompting providers to reassess their sourcing strategies. As a result, some vendors are accelerating partnerships with domestic manufacturers or shifting to cloud-native delivery models to mitigate margin pressures.
Furthermore, regulatory complexity associated with compliance frameworks has increased in tandem with tariff-induced supply chain diversification. Organizations balancing risk management with adherence to data protection regulations now face additional scrutiny when integrating third-party security services, particularly if hardware-based modules originate from jurisdictions subject to elevated duties. Consequently, service providers are increasingly offering hybrid delivery options that blend virtualized functions with software-defined controls, allowing clients to maintain compliance without incurring prohibitive import costs.
In addition, the ripple effects of tariff policy have extended to pricing negotiations, compelling both large enterprises and small-to-medium businesses to seek greater transparency around total cost of ownership. Providers that proactively address these concerns by offering consumption-based billing and bundled service packages are gaining competitive advantage, fostering more resilient engagement models that accommodate fluctuating economic and policy landscapes.
Unveiling Key Segmentation Insights Across Service Types, Pricing Models, Deployment Options, Organization Sizes, and Industry Verticals
The Security-as-a-Service market encompasses a diverse array of solution categories, each tailored to address specific organizational requirements and risk profiles. Segmentation based on service type reveals that cloud access brokers are pivotal for enforcing data protection across APIs and proxy gateways, while endpoint security-as-a-service delivers antivirus and advanced detection and response capabilities directly to devices. Identity-as-a-service offerings bolster authentication frameworks through multi-factor methods, privileged access management, and single sign-on, whereas managed detection and response packages provide continuous threat surveillance, incident resolution, and actionable intelligence. Additionally, network security services mitigate distributed denial-of-service attacks and act as virtual firewalls, complemented by security information and event management solutions that centralize log data and monitor user behaviors.
Shifting to pricing models, pay-as-you-go structures enable organizations to pay solely for actual consumption through hourly or usage-based mechanisms, in contrast to subscription frameworks where annual or monthly commitments may deliver lower unit costs. Deployment variances further delineate cloud-hosted platforms versus on-premise infrastructures, catering to entities with distinct governance and performance requisites. Organizational scale also shapes demand patterns, as large enterprises often require comprehensive, integrated suites, while small and medium-sized entities prioritize modular, cost-effective options. Vertical markets such as financial services, government, healthcare, technology, manufacturing, and retail each impose unique compliance and operational imperatives that drive tailored feature sets and service bundling strategies.
This comprehensive research report categorizes the Security-as-a-Service market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Service Type
- Pricing Model
- Deployment Model
- Organization Size
- Industry Vertical
Examining Regional Dynamics and Differential Growth Patterns Across the Americas, Europe Middle East Africa, and Asia-Pacific Markets
Regional markets exhibit differentiated growth trajectories and adoption drivers for Security-as-a-Service solutions. In the Americas, enterprises continue to prioritize advanced threat detection and data regulatory compliance, fueled by stringent privacy legislation and high-profile cyber incidents. Consequently, providers with strong local support networks and expertise in regional mandates are well positioned to capitalize on demand for integrated security suites and managed services.
In Europe, the Middle East, and Africa, regulatory harmonization under frameworks such as GDPR and emerging data sovereignty requirements have spurred investments in identity protection and information governance tools. Meanwhile, Middle Eastern and North African sectors are emphasizing cloud migration accelerations, creating opportunities for flexible security-as-a-service deployments that minimize upfront capital outlays.
Asia-Pacific markets are characterized by rapid digital transformation in industries ranging from manufacturing to e-commerce. This growth is driving adoption of endpoint and network security-as-a-service offerings, with a specific focus on automated incident response and continuous monitoring. Furthermore, the expanding startup ecosystem in the region is leveraging consumption-based pricing to access enterprise-grade security controls without the constraints of traditional licensing models.
This comprehensive research report examines key regions that drive the evolution of the Security-as-a-Service market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Security-as-a-Service Providers: Strategic Initiatives, Innovation Focus, and Competitive Positioning Insights
Leading service providers in the Security-as-a-Service domain are distinguishing themselves through targeted investments in artificial intelligence, strategic alliances, and vertical market specialization. Some innovators are integrating machine learning engines into their platforms to enhance predictive threat analytics, thereby reducing false positives and accelerating response times. Others have forged cloud-native partnerships, embedding their services within major infrastructure environments to deliver seamless policy orchestration and unified management dashboards.
Competitive positioning is also influenced by go-to-market strategies, with certain vendors focusing on channel ecosystems to extend reach into midsized and regional accounts. Strategic alliances with compliance specialists and professional services firms are creating bundled value propositions that address both technical and regulatory challenges. Moreover, the rise of platform consolidation is prompting key providers to broaden their portfolios through acquisitions and organic feature development, ensuring that clients can centralize security operations within a single pane of glass.
In addition, companies that excel in customer success-offering tailored onboarding, continuous training programs, and proactive advisory services-are elevating their retention rates and creating referenceable case studies. This customer-centric focus underscores the importance of aligning innovation roadmaps with evolving client requirements, reinforcing trust and long-term partnership opportunities.
This comprehensive research report delivers an in-depth overview of the principal market players in the Security-as-a-Service market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Accenture plc
- AT&T Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- Fortinet, Inc.
- International Business Machines Corporation
- Microsoft Corporation
- Okta, Inc.
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- Rapid7, Inc.
- Secureworks Corp.
- SentinelOne, Inc.
- Sophos Ltd.
- Trend Micro Incorporated
- Trustwave Holdings, Inc.
- Verizon Communications Inc.
- Wipro Limited
- Zscaler, Inc.
Actionable Strategic Recommendations for Industry Leaders to Enhance Security Posture, Operational Efficiency, and Market Competitiveness
Industry leaders should prioritize the adoption of zero-trust frameworks, ensuring that every access request is continuously authenticated and authorized. By integrating these principles within security-as-a-service platforms, organizations can enforce least-privilege access and dynamically adapt policies based on real-time threat intelligence. Furthermore, automating incident detection and response workflows through AI-driven orchestration will accelerate containment efforts and reduce reliance on manual processes.
In addition, executives must evaluate hybrid delivery models that blend cloud-native services with localized virtualized controls to balance performance, regulatory compliance, and cost efficiency. Leveraging consumption-based pricing can optimize budget allocation, while subscription bundles can simplify vendor management. Collaboration with strategic channel partners and specialist consultancies will also increase implementation success and ensure alignment with industry-specific compliance mandates.
Lastly, investment in continuous training and awareness programs for security teams and end users remains critical. By fostering a culture of cybersecurity vigilance and proficiency, enterprises can enhance their defensive posture and ensure seamless adoption of new security-as-a-service capabilities. This holistic strategy will drive resilience, operational agility, and sustained competitive advantage.
Insights into Rigorous Research Methodologies Employed to Analyze Security-as-a-Service Market Trends and Stakeholder Perspectives
This market analysis draws upon a rigorous, multi-phase research methodology that combines primary and secondary data sources. Initially, in-depth interviews were conducted with senior security executives, solution architects, and channel partners to capture firsthand perspectives on adoption drivers, implementation challenges, and future priorities. These qualitative insights were complemented by surveys deployed across a cross-section of enterprise and mid-market organizations to quantify sentiment on service preferences, pricing dynamics, and operational outcomes.
Secondary research involved an extensive review of industry publications, regulatory documents, and academic journals to contextualize emerging threat trends and policy developments. Meanwhile, competitive profiling leveraged digital footprint analysis, earnings call transcripts, and patent filings to map vendor innovation trajectories and partnership ecosystems. Quantitative data triangulation was achieved by cross-referencing survey findings, publicly disclosed financial metrics, and procurement tender records, ensuring robustness and validity of insights.
Finally, all findings underwent iterative validation through expert panel reviews, where leading practitioners and consultants provided feedback to refine assumptions and interpret results. This comprehensive approach ensures that the analysis accurately reflects the current state of Security-as-a-Service, equipping stakeholders with actionable intelligence for strategic decision-making.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Security-as-a-Service market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Security-as-a-Service Market, by Service Type
- Security-as-a-Service Market, by Pricing Model
- Security-as-a-Service Market, by Deployment Model
- Security-as-a-Service Market, by Organization Size
- Security-as-a-Service Market, by Industry Vertical
- Security-as-a-Service Market, by Region
- Security-as-a-Service Market, by Group
- Security-as-a-Service Market, by Country
- United States Security-as-a-Service Market
- China Security-as-a-Service Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 2226 ]
Concluding Perspectives on the Imperatives, Challenges, and Future Readiness of Security-as-a-Service in Evolving Threat Landscapes
Security-as-a-Service has emerged as a pivotal paradigm for organizations seeking to modernize their cybersecurity defenses while optimizing operational agility. The convergence of cloud migration, AI-driven analytics, and zero-trust architectures is reshaping how enterprises perceive and implement security controls. As tariff policies and regional regulatory shifts introduce new complexities, adaptive strategies that blend consumption-based models with hybrid deployment options are proving most effective.
Key segmentation insights underscore that a one-size-fits-all approach is no longer viable; organizations must carefully evaluate service types, pricing frameworks, and deployment configurations based on their unique risk profiles and compliance obligations. Regional analyses further highlight that success hinges on localized expertise, regulatory alignment, and flexible engagement models. Meanwhile, competitive dynamics reveal that innovation leaders are those who combine technological advancements with customer-centric support and strategic alliances.
In conclusion, embracing Security-as-a-Service requires a holistic mindset that balances technical sophistication, economic pragmatism, and continuous learning. By adopting the actionable recommendations outlined, enterprises can not only address current threat landscapes but also position themselves for sustained resilience and growth in an ever-evolving digital world.
Drive Business Resilience and Security Maturity by Engaging Ketan Rohom to Access the Comprehensive Security-as-a-Service Market Analysis
For decision-makers seeking to fortify their security posture with innovative, scalable solutions, partnering with Ketan Rohom represents a strategic opportunity to accelerate risk mitigation and operational resilience. As Associate Director of Sales & Marketing, Ketan brings extensive expertise in aligning tailored security-as-a-service offerings with the unique needs of organizations across diverse industries. Whether your enterprise is navigating complex compliance requirements, planning a multi-cloud transformation, or seeking advanced threat detection capabilities, a conversation with Ketan can clarify the most effective roadmap to success.
Engagement begins with a personalized consultation that explores your organization’s current security infrastructure, evaluates critical vulnerabilities, and identifies high-impact areas for optimization. This consultative approach ensures that recommended solutions are fully aligned with your strategic objectives and budget parameters. From evaluating API-based cloud access security brokers to integrating managed detection and response services, Ketan can guide you through the intricacies of each service type, pricing model, and deployment scenario to craft a comprehensive, future-proof security program.
Take the next step toward robust, cost-effective protection by reaching out to Ketan Rohom. His deep understanding of market trends, regulatory landscapes, and emerging threat vectors will empower your team to make informed decisions and maximize return on investment. Don’t leave your organization’s security to chance-connect with Ketan through LinkedIn to schedule a detailed briefing and discover how a tailored security-as-a-service strategy can safeguard your digital assets and support your long-term growth ambitions.

- How big is the Security-as-a-Service Market?
- What is the Security-as-a-Service Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




