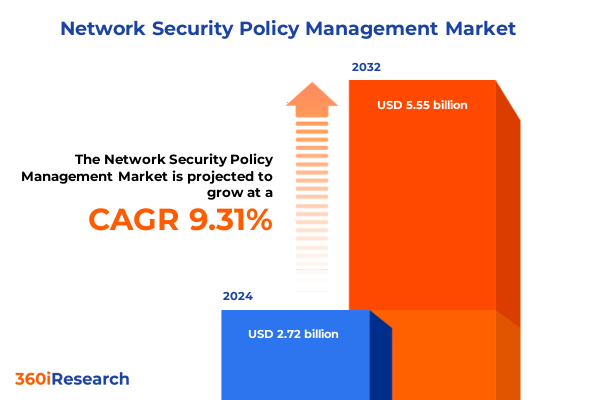
The Network Security Policy Management Market size was estimated at USD 2.96 billion in 2025 and expected to reach USD 3.24 billion in 2026, at a CAGR of 9.36% to reach USD 5.55 billion by 2032.
Driving Enterprise Resilience Through Robust Network Security Policy Management: An Executive Overview of Market Dynamics and Strategic Imperatives
The accelerating pace of digital transformation has elevated network security policy management from a niche operational concern to a critical strategic priority for organizations of all sizes. As enterprises navigate increasingly sophisticated cyber threats and complex regulatory requirements, robust policy frameworks serve as the foundation for proactive defense. This executive summary distills the most pressing drivers, key trends, and strategic considerations that shape the current market landscape, enabling decision makers to align investments with emerging imperatives.
In an era where hybrid work models, cloud migrations, and converged network architectures intersect, security policy management demands a cohesive approach that spans on-premises, private cloud, and public cloud environments. The insights presented here draw upon comprehensive research into deployment preferences, functional needs, and service expectations. By synthesizing these dimensions, this overview equips leaders with the intelligence needed to future-proof their infrastructure, streamline policy enforcement, and maintain compliance across dynamic ecosystems.
Navigating Unprecedented Shifts in Network Security Policy Management Fueled by Cloud Proliferation AI Integration and Zero Trust Architectures
Rapid technological advances and shifting threat actor tactics have converged to reshape the network security policy management landscape in fundamental ways. Foremost among these transformations is the widespread adoption of cloud-native and hybrid architectures, which demand policy frameworks capable of enforcing consistent controls across distributed environments. Consequently, organizations now prioritize platforms that enable centralized policy definition while automating enforcement at the network edge and within virtualized workloads.
Parallel to infrastructural evolution is the rise of artificial intelligence and machine learning as enablers of policy automation. By embedding predictive analytics into policy engines, enterprises can proactively identify anomalous behavior, adapt controls in real time, and reduce manual overhead. This convergence of AI-driven insights with traditional rule-based frameworks is giving rise to intelligent, adaptive policy solutions that respond dynamically to emerging threats.
Moreover, the industry is witnessing a shift from perimeter-centric security toward zero trust architectures, where every access request is continuously evaluated against policy context, user identity, and device posture. This paradigm shift necessitates granular, identity-aware policy controls that seamlessly integrate with identity and access management systems. As organizations embrace zero trust, network security policy management evolves into a strategic capability that underpins risk reduction and compliance initiatives alike.
Unpacking the Cumulative Impact of 2025 US Tariffs on Network Security Policy Management Supply Chains and Cost Structures in Technology Procurement
In 2025, a series of tariff adjustments enacted by the United States government have exerted significant pressure on technology procurement and supply chain dynamics. Network equipment and appliances, often sourced from international manufacturers, have become subject to elevated duties, driving up capital expenditures for enterprises seeking to refresh switches, firewalls, and next-generation security appliances. The additional cost burden has compelled many organizations to reallocate budgets, delaying planned hardware upgrades in favor of software-defined or virtualized alternatives.
These tariff-induced cost increases have also reverberated through channel partner ecosystems, prompting distributors and resellers to recalibrate pricing models and renegotiate vendor agreements. In response, solution providers have accelerated investments in domestic production and localized support services to mitigate supply chain risks and currency exposure. As a result, the market is experiencing a strategic realignment, with greater emphasis on software-centric policy management platforms that can be deployed independently of physical appliances, thereby insulating enterprises from future tariff volatility.
Illuminating Key Insights Across Deployment Models Components Organization Sizes Verticals and Service Channels Shaping Network Security Policy Management
A granular examination of market segmentation reveals distinct preferences and adoption drivers across deployment models, component requirements, organization sizes, vertical industries, channel strategies, and service offerings. Enterprises with fully cloud-based infrastructures increasingly favor public cloud environments for their scalability and rapid provisioning, while private cloud deployments attract organizations with stringent data sovereignty and compliance mandates. Hybrid environments, bridging on-premises investments with cloud elasticity, remain prevalent among established businesses seeking to modernize incrementally without sacrificing control.
On the component front, policy management for access control has become indispensable as remote and hybrid work models proliferate. Simultaneously, firewall policy management continues to command significant attention, given its role in enforcing perimeter and internal segmentation controls. Compliance policy management solutions are gaining momentum as regulatory frameworks grow more complex, while VPN policy management retains importance for secure connectivity to corporate assets.
Organization size profoundly influences purchasing decisions and platform capabilities. Large enterprises often adopt modular, customizable policy suites that integrate deeply with existing security operations centers, whereas small and medium enterprises gravitate toward turnkey offerings with managed services to offset limited in-house expertise. Similarly, vertical industries display divergent trajectories: financial services and government sectors prioritize robust compliance and audit capabilities, healthcare entities focus on patient data protection, and IT and telecom firms pursue agility and orchestration to support high-volume traffic demands.
Channel partnerships continue to play a pivotal role in solution delivery, as specialized resellers and integrators offer value-added services that streamline deployment. At the same time, vendor direct sales teams leverage deep product expertise to secure large enterprise contracts. Service models further differentiate market players: managed service offerings cater to organizations seeking end-to-end oversight, while professional services engage clients in customized implementations and ongoing advisory support. Together, these segmentation insights illuminate the multifaceted nature of solution demand and underscore the importance of tailored go-to-market approaches.
This comprehensive research report categorizes the Network Security Policy Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Deployment Model
- Organization Size
- Delivery Model
- Application
- Industry Vertical
- Channel
Delineating Regional Nuances in Network Security Policy Management Trends Across the Americas EMEA and Asia Pacific Markets and Operational Strategies
Regional dynamics in network security policy management reflect varying maturity levels, regulatory landscapes, and growth trajectories. In the Americas, the United States and Canada lead adoption through investments in cloud-native architectures and robust compliance frameworks. Organizations in this region emphasize integration with existing security information and event management systems, seeking unified visibility across hybrid estates. Latin American enterprises are accelerating digital transformation projects, often prioritizing managed services to bridge skill gaps and navigate evolving data protection regulations.
Europe, Middle East, and Africa markets present a complex tapestry of regulatory drivers, with GDPR serving as a foundational influence across the European Union. Enterprises here demand fine-grained policy controls for data residency and user privacy, fueling demand for solutions that support granular classification and audit capabilities. In the Middle East and Africa, government initiatives aimed at digital sovereignty and critical infrastructure protection are spurring investments in both on-premises and cloud policy platforms, often delivered through government-approved local partners.
Asia-Pacific markets exhibit some of the fastest growth rates, driven by aggressive cloud adoption in emerging economies and government mandates for cybersecurity resilience. China and India are investing heavily in indigenous technology solutions, prompting multinational vendors to establish local development centers and partner networks. Australia and Japan maintain sophisticated security ecosystems, integrating zero trust and AI-driven policy tools to safeguard critical industries from increasingly sophisticated threats. Across the region, the convergence of cloud-first strategies and advanced threat landscapes underscores the imperative for adaptive, scalable policy management frameworks.
This comprehensive research report examines key regions that drive the evolution of the Network Security Policy Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Network Security Policy Management Solution Providers Driving Innovation Partnerships and Competitive Strategies in a Rapidly Evolving Landscape
Industry leaders and challenger brands alike are forging the competitive contours of the network security policy management market through differentiated technology portfolios and strategic collaborations. Established vendors leverage decades of threat intelligence and enterprise deployment experience to bolster their policy engines with machine learning-powered anomaly detection and automated remediation workflows. These incumbents often extend their ecosystems through alliances with SIEM and SOAR providers, enabling seamless incident response orchestration.
Concurrently, nimble upstarts are carving out market share by delivering cloud-native, API-driven policy platforms designed for rapid integration with DevOps pipelines. Their adoption of container-aware policy agents and micro-segmentation capabilities appeals to organizations adopting Kubernetes and service mesh architectures. Several emerging firms have also embraced open standards to facilitate interoperability, earning traction among clients seeking to avoid vendor lock-in.
Partnership strategies further differentiate top performers. Vendors with robust channel programs cultivate specialized integrators to handle complex implementations and compliance audits, while direct-to-enterprise teams focus on large-scale digital transformation projects. In addition, alliances with cloud hyperscalers ensure optimized policy enforcement at the edge of public cloud regions. Collectively, these competitive maneuvers emphasize the critical role of ecosystem orchestration and innovation velocity in maintaining market leadership.
This comprehensive research report delivers an in-depth overview of the principal market players in the Network Security Policy Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- AlgoSec Inc.
- Amazon Web Services, Inc.
- Aviatrix, Inc.
- Barracuda Networks, Inc.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Extreme Networks, Inc.
- F5, Inc.
- FireMon, LLC
- Forcepoint LLC
- Forescout Technologies, Inc.
- Fortinet, Inc.
- Huawei Technologies Co., Ltd.
- Illumio, Inc.
- International Business Machines Corporation
- Juniper Networks, Inc. by Hewlett Packard Enterprise Company
- Microsoft Corporation
- Open Text Corporation
- Palo Alto Networks, Inc.
- Radware Ltd.
- SolarWinds Worldwide, LLC
- Sophos Ltd.
- Trend Micro Incorporated
- Tufin
Actionable Strategic Imperatives for Industry Leaders to Enhance Security Posture Drive Operational Efficiency and Foster Compliance in Policy Management
To capitalize on emergent opportunities and fortify security postures, industry leaders should adopt a unified policy management platform that spans on-premises, private cloud, and public cloud environments. By consolidating policy definition and deployment through a single pane of glass, organizations can reduce configuration drift and ensure consistent enforcement across dynamic workloads. Integrating this platform with identity and access management solutions further reinforces zero trust principles and streamlines compliance reporting.
Furthermore, leaders must prioritize the infusion of artificial intelligence and automation into policy workflows. Implementing predictive analytics to identify policy deviations before they manifest as security incidents empowers teams to shift from reactive to proactive postures. Automated policy tuning, leveraging real-time telemetry, minimizes manual effort and accelerates incident response, enabling security teams to focus on strategic initiatives rather than repetitive rule updates.
Strategic collaboration with trusted managed service providers can address resource constraints and accelerate time to value. Outsourcing day-to-day policy monitoring and enforcement allows internal teams to concentrate on policy design and governance. Additionally, investing in continuous training programs ensures that personnel remain proficient in the latest frameworks and threat landscapes. Finally, cultivating strong relationships with technology partners, including cloud providers and channel integrators, provides early access to roadmaps and co-innovation opportunities that keep policy management practices at the cutting edge.
Employing Rigorous Qualitative and Quantitative Research Methodologies to Derive Actionable Intelligence in Network Security Policy Management Analysis
This analysis employed a rigorous research methodology, combining primary and secondary data collection to ensure depth and accuracy. Primary research comprised in-depth interviews with senior security architects, network engineers, and compliance officers across multiple industries. These conversations yielded qualitative insights into deployment preferences, policy challenges, and strategic priorities.
Secondary research involved a comprehensive review of industry publications, regulatory guidelines, and vendor briefings. Data triangulation techniques were applied to validate emerging trends and identify areas of convergence. The research process also incorporated case studies of successful policy management implementations, enabling the extraction of best practices and lessons learned. Quality assurance protocols, including peer reviews and fact-checking, were implemented throughout to guarantee the credibility and relevance of the findings.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Network Security Policy Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Network Security Policy Management Market, by Component
- Network Security Policy Management Market, by Deployment Model
- Network Security Policy Management Market, by Organization Size
- Network Security Policy Management Market, by Delivery Model
- Network Security Policy Management Market, by Application
- Network Security Policy Management Market, by Industry Vertical
- Network Security Policy Management Market, by Channel
- Network Security Policy Management Market, by Region
- Network Security Policy Management Market, by Group
- Network Security Policy Management Market, by Country
- United States Network Security Policy Management Market
- China Network Security Policy Management Market
- Competitive Landscape
- List of Figures [Total: 19]
- List of Tables [Total: 1908 ]
Synthesizing Critical Findings to Chart the Future of Network Security Policy Management and Empower Decision Makers with Clear Strategic Direction
This executive summary has distilled critical insights into the forces reshaping network security policy management, from the impact of new tariffs to the nuanced demands of various deployment models, components, and regions. The convergence of cloud proliferation, AI-driven automation, and zero trust frameworks underscores the imperative for integrated, adaptive policy platforms that can evolve with organizational needs.
As the market continues to mature, decision makers must navigate a complex ecosystem of established vendors, emerging challengers, and service providers. By aligning policy management strategies with clearly defined architectures, leveraging automation to reduce manual overhead, and forging strategic partnerships, enterprises can achieve both resilience and agility. Ultimately, proactive policy governance will determine the ability to withstand evolving threats and regulatory pressures, charting a course toward sustained security and operational excellence.
Take the Next Step to Secure Your Network Security Policy Management Strategy with Expert Insights from Associate Director Ketan Rohom Today
To secure a comprehensive understanding of the evolving network security policy management landscape and gain access to in-depth strategic analysis, reach out directly to Ketan Rohom, Associate Director of Sales & Marketing. He can guide you through tailored insights and provide a detailed demonstration of the report’s findings. Engaging with Ketan ensures you have the expert support needed to align your organization’s security posture with the latest best practices and emerging trends. Contact Ketan today to acquire the full market research report and empower your team with actionable intelligence.

- How big is the Network Security Policy Management Market?
- What is the Network Security Policy Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




