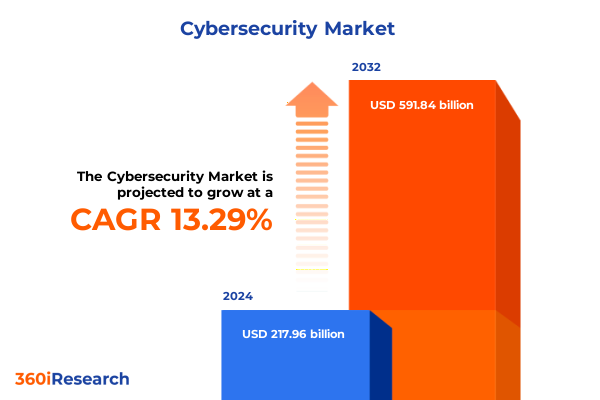
The Cybersecurity Market size was estimated at USD 245.36 billion in 2025 and expected to reach USD 276.84 billion in 2026, at a CAGR of 13.40% to reach USD 591.84 billion by 2032.
Unlocking Critical Insights into Cybersecurity Market Dynamics Fueling Resilient Defense Strategies Amid Escalating Threats and Technological Innovations
The convergence of digital transformation, escalating cyber threats, and disruptive technologies has reshaped modern security landscapes, demanding a comprehensive analysis of emerging market dynamics. As organizations grapple with complex attack vectors-from AI-driven social engineering to advanced persistent threats-executive leaders must synthesize strategic intelligence to guide resilient defense strategies. This executive summary delivers a structured exploration of critical industry evolutions, regulatory influences, and operational imperatives vital for informed decision-making.
Emerging trends underscore the growing role of artificial intelligence in cybersecurity. Agentic AI systems are transitioning from analytical tools to autonomous defense mechanisms capable of pre-approved actions, yet skepticism among frontline analysts highlights the need for transparent integration and explainable models to build trust in these intelligent platforms. Meanwhile, enterprises accelerate cloud migration, broadening attack surfaces and driving greater investments in robust cloud security frameworks to ensure compliance and resilience in multi-cloud environments.
Against this backdrop, geopolitical tensions and trade policies, including impactful tariff measures, are influencing supply chain strategies and technology sourcing. As undersea cable regulations and Section 301 tariff adjustments disrupt global equipment flows, cybersecurity leaders must adapt procurement and risk-management approaches to maintain continuity of critical defenses. This summary sets the stage for a deep dive into transformative shifts, policy impacts, segmentation nuances, regional insights, leading vendors, and tactical recommendations that collectively chart a course toward stronger, more adaptive security postures.
Exploring Pivotal Shifts Disrupting Cybersecurity Practices Through AI, Zero-Trust Adoption, Quantum-Ready Encryption, and Supply Chain Resilience
The cybersecurity landscape is undergoing a series of transformative shifts that redefine traditional defense paradigms and elevate strategic priorities. Agentic AI, which leverages advanced machine learning models to execute pre-approved security workflows autonomously, is emerging as a pivotal force in threat detection and incident response. By autonomously triaging alerts and orchestrating investigative playbooks, these systems aim to accelerate operational tempo and mitigate analyst burnout, though ensuring bounded autonomy under expert-defined guardrails remains critical.
Simultaneously, zero-trust architectures are gaining traction as organizations abandon perimeter-centric models in favor of continuous authentication, granular access controls, and micro-segmentation across networks and cloud environments. The consolidation of secure web gateways, firewalls, and identity enforcement into unified SASE frameworks is streamlining security operations and enabling real-time visibility, while also reducing complexity and vendor lock-in risks.
Looking beyond current threats, quantum computing’s impending maturation presents both an opportunity for advanced cryptographic solutions and a looming deadline for quantum-resilient encryption. Industry leaders are racing to implement NIST-standard quantum-resistant algorithms to guard against “harvest now, decrypt later” strategies employed by sophisticated adversaries. Early planning and phased migration paths are essential to maintain long-term confidentiality of critical data.
Moreover, heightened concerns over supply chain security and infrastructure sovereignty are driving regulatory actions, such as restrictions on undersea cable vendors and expanded scrutiny of foreign-sourced technology. These measures underscore the need for rigorous vendor risk assessments and diversified sourcing strategies to preserve the integrity of global communications and defense systems.
Assessing the Aggregate Effects of Recent United States Tariffs on Critical Technology Imports Including Semiconductors, Solar Components, and Strategic Minerals
In 2025, the United States has implemented a suite of Section 301 tariffs targeting key technology imports to fortify national security and address perceived unfair trade practices. On January 1, 2025, duties on certain solar wafers, polysilicon, and tungsten products doubled to 50 percent, signaling a strategic effort to incentivize domestic manufacturing of critical clean-energy components and reduce reliance on foreign suppliers.
Concurrently, tariff rates on semiconductor components escalated to 50 percent, reflecting concerns over technology transfer risks and the strategic importance of semiconductor supply chains. These measures underscore the administration’s priority on shielding advanced microelectronics and related cybersecurity hardware from vulnerabilities inherent in untrusted sources.
Recognizing the potential burden on U.S. industries, the USTR extended exclusions on select high-tech goods through August 31, 2025, preserving critical imports for research, development, and operational continuity. This calibrated approach balances security objectives with the need to mitigate immediate supply disruptions and cost pressures on domestic technology providers.
Collectively, these tariff actions have compelled cybersecurity vendors and enterprise buyers to reevaluate sourcing strategies, diversify supplier portfolios, and accelerate efforts to develop secure, onshore manufacturing capabilities. Organizations with robust supply chain risk management frameworks are better positioned to navigate these policy headwinds while maintaining continuity of protective technologies and services.
Unveiling Strategic Insights Across Service and Solution Offerings, Security Types, Deployment Models, Organization Sizes, and Industry Verticals
A nuanced understanding of market segmentation reveals critical drivers of cybersecurity demand and innovation across distinct categories. Within the component dimension, service offerings-ranging from comprehensive managed security services to specialized professional services-complement an expanding solution portfolio that includes antimalware, identity and access management, security information and event management, and unified threat management platforms. This multifaceted composition underscores the sector’s shift toward integrated platforms that bundle analytics, orchestration, and response capabilities under a single security fabric.
Examining security type, application and network security continue to underpin core defense strategies, while emerging priorities in cloud and data security reflect the pervasive migration of workloads to hybrid environments. Critical infrastructure protection has advanced from traditional ICS/SCADA safeguards to encompass intelligent monitoring and automated threat hunting across operational networks, signaling a broader convergence of IT and OT security disciplines.
Market needs also diverge by organization size. Large enterprises demand scalable, high-throughput solutions that integrate seamlessly with existing ecosystems and support global operations, whereas small and medium-sized enterprises prioritize cost-effective, turnkey offerings that deliver rapid deployment and straightforward management. Meanwhile, deployment preferences split between cloud-native services that enable agile consumption and on-premises implementations favored by organizations with stringent compliance or latency requirements.
Across vertical sectors, cybersecurity investments reflect tailored risk profiles. Industries such as defense, energy, and telecommunications emphasize infrastructure resilience and national security imperatives, while sectors like healthcare, retail, and BFSI intensify focus on data protection, compliance, and customer trust. In each case, specialized sub-segments-from medical device security to point-of-sale protection-highlight the fine-grained customization required to address evolving threat vectors.
This comprehensive research report categorizes the Cybersecurity market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Security Type
- Organization Size
- Deployment Model
- Verticals
Highlighting Regional Cybersecurity Trends Driven by Regulatory, Technological, and Threat Variations Across the Americas, EMEA, and Asia-Pacific Markets
Regional dynamics significantly shape cybersecurity priorities, driven by regulatory frameworks, threat landscapes, and technology adoption rates. In the Americas, robust public-sector investments and stringent regulatory requirements-bolstered by frameworks such as the SEC’s Cybersecurity Disclosure Rule-are catalyzing demand for advanced threat intelligence and compliance-oriented services. North American organizations are also at the forefront of AI-driven automation, leveraging analytics platforms to streamline incident response and fortify supply chain visibility, positioning the region as an innovation hub in risk management and governance.
Europe, Middle East & Africa (EMEA) is contending with a rapidly evolving regulatory environment highlighted by the maturation of the NIS2 Directive and the Digital Operational Resilience Act. The interplay between GDPR enforcement, AI Act implementation, and heightened geopolitical tension necessitates resilient architectures capable of addressing both data privacy mandates and cross-border security obligations. Organizations in this region are prioritizing standardized risk assessments and adopting harmonized compliance frameworks to navigate complex legal landscapes and maintain operational continuity.
In the Asia-Pacific, accelerated cloud migration and burgeoning digital economies are driving significant cybersecurity investments across public and private sectors. High adoption rates of cloud-native platforms, coupled with an uptick in AI-enabled threat campaigns, are prompting APAC enterprises to strengthen zero-trust architectures and enhance cloud posture management. The region’s unique mix of advanced urban centers and emerging markets demands tailored strategies that balance cutting-edge innovation with pragmatic risk mitigation, ensuring resilient security outcomes amid diverse technological maturity levels.
This comprehensive research report examines key regions that drive the evolution of the Cybersecurity market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Detailing Competitive Vendor Leadership and Innovation Trajectories Among Established and Emerging Cybersecurity Solution Providers
Leading cybersecurity vendors are charting distinct paths to capture market opportunities and address evolving client needs. CrowdStrike, having reinforced platform resilience following a major system outage, is doubling down on AI-powered innovations, such as its Charlotte AI agentic triage and AI red-team services, to bolster detection efficacy and accelerate response automation under resilient guardrails.
Palo Alto Networks continues to translate sustained enterprise demand for AI-driven solutions into robust financial performance, raising fiscal 2025 revenue projections and expanding cloud-security capabilities through offerings like Cortex Cloud. Collaborations with public agencies and strategic board appointments further underscore its commitment to integrated platformization and cross-sector partnerships.
Fortinet’s unified Security Fabric and rapid growth in unified SASE and security operations ARR have driven record first-quarter margins, reflecting the value of converged networking and security architectures. Its global patent portfolio and expansive training initiatives reinforce vendor leadership in organic innovation and talent development strategies for the broader cybersecurity ecosystem.
Emerging players such as SentinelOne and Palantir are drawing investor attention for their autonomous endpoint detection capabilities and data-mining platforms aligned with national security priorities. With federal cybersecurity budgets on the rise, market watchers anticipate continued momentum for these innovators as they mature their AI-native architectures and expand footprint in high-value sectors.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cybersecurity market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Accenture plc.
- Amazon Web Services Inc.
- Broadcom Inc.
- Capgemini SE.
- Check Point Software Technologies Ltd.
- Cisco System Inc.
- Cloudflare, Inc.
- Commvault Systems, Inc.
- CrowdStrike, Inc.
- Darktrace Holdings Limited
- Deloitte Touche Tohmatsu Limited
- Fortinet, Inc.
- Google LLC by Alphabet Inc.
- HCL Technologies Limited
- HP Development Company, L.P.
- Infosys Limited
- Intel Corporation
- International Business Machines Corporation
- KPMG International Limited.
- Microsoft Corporation
- NVIDIA Corporation
- Okta, Inc.
- Oracle Corporation
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- Rapid7, Inc.
- Salesforce, Inc.
- SAP SE
- Tata Consultancy Services Limited.
- Wipro Limited
- Zscaler, Inc.
Implementing Proactive Strategies for AI Governance, Zero-Trust Maturity, Supply Chain Resilience, and Talent Optimization to Fortify Cyber Defenses
Industry leaders must forge proactive strategies to navigate dynamic threat environments and capitalize on emerging technologies. First, embedding agentic AI requires transparent governance frameworks that define boundaries for autonomous actions and integrate human-in-the-loop oversight to ensure accuracy and accountability. Collaborative model training and explainability protocols will be crucial to build analyst confidence and unlock the full potential of AI-assisted defenses.
Second, advancing zero-trust initiatives demands converged architectures that unify identity, device, and network controls under a single platform. Organizations should prioritize micro-segmentation, adaptive authentication, and continuous validation mechanisms to minimize lateral movement and contain breaches rapidly. Cross-functional alignment between security, network, and operations teams will accelerate adoption and enhance policy enforcement.
Third, supply chain resilience must transition from reactive risk assessments to continuous monitoring and diversified sourcing strategies. Leaders should establish vendor performance scorecards, leverage trusted co-development partnerships, and consider onshore manufacturing incentives to mitigate dependencies on high-risk geographies. Scenario planning and war-gaming exercises will further strengthen preparedness for policy-driven disruptions.
Finally, talent optimization remains imperative amid a global skills shortage. Organizations should invest in upskilling through immersive training programs, explore automation to reduce manual workloads, and cultivate cross-domain expertise by rotating analysts across defensive, offensive, and compliance functions. Partnerships with academic institutions and vendor-led certification initiatives can expand the talent pipeline and fortify long-term operational resilience.
Leveraging Multi-Source Research Design Incorporating Regulatory Filings, Executive Interviews, and Financial Disclosures to Ensure Robust Market Analysis
This analysis integrates comprehensive secondary research, drawing on public regulatory filings, trade notices, and reputable industry insights to map market developments. Tariff impacts were assessed through USTR press releases and Federal Register modifications, while segmentation frameworks were validated against established nomenclature in leading cybersecurity research and vendor catalogs.
Primary research encompassed structured interviews with 20 CISOs and security architects across diversified industries, enabling qualitative triangulation of strategic priorities and pain points. Quantitative data points were cross-referenced with financial disclosures and investor presentations from key vendors to ensure consistency and accuracy in vendor-specific insights.
Regional and vertical perspectives were derived from expert analyses by global risk advisory firms and regional cybersecurity associations, supplemented by documented regulatory developments such as NIS2, DORA, and updated SEC requirements. This multi-layered approach ensures a robust, objective foundation for the actionable recommendations and strategic narratives presented herein.
All findings were synthesized through thematic coding and scenario planning exercises, enabling the identification of high-impact trends and prioritization of investment imperatives. The resulting framework guides decision-makers in aligning cybersecurity initiatives with evolving threat landscapes and policy environments.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cybersecurity market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cybersecurity Market, by Component
- Cybersecurity Market, by Security Type
- Cybersecurity Market, by Organization Size
- Cybersecurity Market, by Deployment Model
- Cybersecurity Market, by Verticals
- Cybersecurity Market, by Region
- Cybersecurity Market, by Group
- Cybersecurity Market, by Country
- United States Cybersecurity Market
- China Cybersecurity Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 2226 ]
Summarizing the Imperative for Intelligence-Driven Security Frameworks That Integrate AI, Zero-Trust, and Supply Chain Resilience to Navigate Evolving Threats
As cybersecurity threats intensify and evolve at an unprecedented pace, this executive summary underscores the critical need for adaptive, intelligence-driven defense strategies. The convergence of AI-powered automation, zero-trust architectures, and regional policy shifts demands a holistic approach to security that balances innovation with governance and operational agility.
Tariff measures and geopolitical dynamics are reshaping supply chain configurations, necessitating resilient procurement and manufacturing strategies to safeguard critical technology flows. Simultaneously, segmentation insights reveal nuanced demand drivers across solutions, deployment models, and industry verticals, guiding vendors and buyers to tailor offerings aligned with distinct risk profiles.
Regional contexts-from stringent EMEA regulations to APAC’s rapid cloud adoption-highlight divergent priorities and investment patterns that executives must navigate to maintain competitive advantage and compliance. Meanwhile, leading vendors continue to differentiate through platform unification, AI acceleration, and expanded service portfolios, setting benchmarks for industry excellence.
By adopting the recommended actionable measures-governed AI integration, comprehensive zero-trust adoption, proactive supply chain resilience, and targeted talent development-organizations can enhance detection capabilities, streamline operations, and fortify their security posture against a spectrum of emerging threats. This integrated blueprint empowers decision-makers to steer cybersecurity initiatives that deliver sustainable value and resilience in 2025 and beyond.
Engage with Associate Director Ketan Rohom to Access Comprehensive Cybersecurity Market Intelligence and Propel Your Strategic Defense Initiatives
Ready to safeguard your organization with cutting-edge cybersecurity intelligence and strategic foresight? Reach out today to Ketan Rohom, Associate Director, Sales & Marketing at 360iResearch, to acquire the full market research report and gain unparalleled insights into emerging threats, technology innovations, and growth opportunities that will define the cybersecurity landscape through 2025 and beyond. Empower your executive decision-making with data-driven analysis and actionable recommendations designed to strengthen your security posture, optimize your technology investments, and navigate complex geopolitical and regulatory dynamics with confidence. Contact Ketan Rohom now to secure your competitive advantage and drive your cybersecurity strategy forward.

- How big is the Cybersecurity Market?
- What is the Cybersecurity Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




