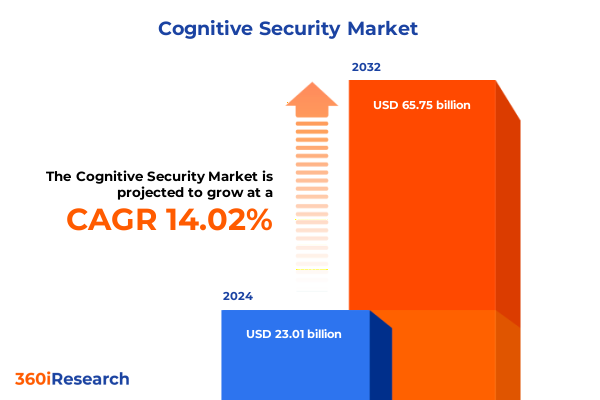
The Cognitive Security Market size was estimated at USD 26.11 billion in 2025 and expected to reach USD 29.64 billion in 2026, at a CAGR of 14.09% to reach USD 65.75 billion by 2032.
Pioneering Cognitive Security as the Next Frontier in Cyber Defense Empowering Organizations with Proactive Threat Intelligence and Adaptive Risk Management
In an era marked by escalating cyber threats and increasingly sophisticated attacks, cognitive security emerges as a transformative paradigm that transcends traditional defense mechanisms. By harnessing advanced artificial intelligence algorithms and behavioral analytics, cognitive security offers a dynamic approach to threat detection and response, continuously learning from new data to anticipate and mitigate risks before they materialize. This proactive stance is rapidly becoming essential for organizations that seek to preserve operational continuity and safeguard sensitive assets.
As enterprises navigate a complex digital landscape where attack surfaces expand daily, cognitive security platforms integrate seamlessly with existing infrastructures, enriching situational awareness across networks, endpoints, and cloud environments. Through a symbiotic relationship between human expertise and machine-driven insight, security teams can prioritize high-impact threats and streamline incident response workflows. This synergy not only enhances the speed and accuracy of threat mitigation but also fosters a culture of continuous improvement in cybersecurity practices.
Moreover, the adaptive nature of cognitive security ensures that defense strategies remain resilient in the face of rapidly evolving attack vectors. By assimilating vast streams of structured and unstructured data-from threat intelligence feeds to user behavior patterns-organizations can maintain a real-time understanding of their risk landscape. Consequently, cognitive security stands at the forefront of next-generation cyber defense, enabling organizations to outmaneuver adversaries and build long-term resilience.
Uncovering the Critical Transformative Shifts in Cognitive Security Landscape Driven by AI Innovation and Evolving Threat Actors
The landscape of cybersecurity is undergoing profound transformation, driven by advances in artificial intelligence, heightened regulatory scrutiny, and the convergence of IT and operational technologies. As threat actors leverage automation and machine learning to launch increasingly complex attacks, defenders are responding with cognitive security platforms that mirror adversarial tactics. In doing so, organizations are shifting from reactive, signature-based defenses to proactive, behavior-driven models that detect anomalies in real time and adapt to emerging threats.
Simultaneously, regulatory environments around the globe are evolving to address data privacy and cross-border information sharing. Mandatory breach notification frameworks, coupled with stringent data protection laws, have compelled organizations to reevaluate their security architectures. By integrating cognitive security solutions, businesses can enhance compliance, generate comprehensive audit trails, and demonstrate due diligence in protecting sensitive information-thereby reducing regulatory exposure and potential financial penalties.
Furthermore, the integration of cognitive security into cloud-native infrastructures has accelerated the adoption of scalable, as-a-service delivery models. Technology providers are embedding cognitive capabilities directly within cloud platforms, enabling seamless deployment and real-time threat intelligence sharing across distributed environments. Collectively, these transformative shifts are redefining defensive postures, enabling security teams to stay ahead of adversaries and support the digital transformation objectives of their organizations.
Analyzing How United States Tariffs Implemented in 2025 Have Disrupted Cognitive Security Supply Chains and Accelerated Indigenous Innovation
The United States’ introduction of targeted tariffs on critical hardware components and AI-accelerating GPUs in 2025 has reverberated across the cognitive security industry. Organizations reliant on imported chipsets and processing units experienced immediate cost escalations, prompting them to explore alternative procurement strategies. In response, many enterprises accelerated their migration to cloud-based cognitive security services, reducing dependence on on-premise hardware while maintaining advanced threat detection capabilities.
In parallel, domestic technology firms have capitalized on the disruption by intensifying local research and development efforts. Hardware manufacturers and cognitive security platform providers are collaborating on indigenous chip designs optimized for machine learning workloads, thereby mitigating supply chain risks and securing strategic autonomy. This shift has not only fostered innovation within the United States but also stimulated broader ecosystem growth, as component suppliers forge partnerships with security software developers to co-engineer end-to-end solutions.
Moreover, the tariffs have triggered a reevaluation of global sourcing models. Organizations are diversifying supply chains by engaging suppliers across Asia-Pacific and Europe, balancing cost considerations with geopolitical stability and logistical resilience. As a result, the industry is witnessing a renaissance in cross-border collaboration, enabling cognitive security vendors to build more robust, geographically distributed manufacturing and support networks. Ultimately, these cumulative impacts underscore the imperative for adaptability and strategic foresight in navigating evolving trade landscapes.
Revealing Key Segmentation Insights Illuminating Component Services Solutions Security Types Technologies Applications Deployment Modes and End User Priorities
The cognitive security market reveals nuanced distinctions across its core components, as enterprises evaluate the balance between services and solutions. On the services front, deployment and integration efforts are critical for ensuring that cognitive algorithms integrate seamlessly within legacy infrastructures, while support and maintenance services deliver continuous system optimization and incident management. Meanwhile, training and consulting services empower security teams to leverage cognitive analytics effectively, translating complex insights into actionable defense strategies. Conversely, solution offerings span behavioral analytics engines that profile user and entity behavior, comprehensive cognitive security platforms that orchestrate multi-vector threat response, security information and event management systems that aggregate telemetry, and specialized threat detection and response platforms designed to automate threat hunting and remediation workflows.
Beyond components, security type segmentation underscores diverse organizational needs. Application security modules focus on identifying vulnerabilities within code and runtime environments, whereas cloud security frameworks protect workloads across public and private clouds. Endpoint security solutions guard against device-based attacks, and network security tools monitor traffic flows for anomalous patterns. Each security domain leverages cognitive capabilities to elevate detection accuracy and reduce false positives, tailoring insights to specific attack surfaces.
Technological innovations further segment the market, with computer vision enabling image-based threat detection, machine learning powering dynamic risk scoring, and natural language processing parsing unstructured text for threat intelligence. Application-centric segmentation highlights anomaly detection mechanisms that spotlight deviations in user behavior, fraud detection and prevention platforms that secure financial transactions, risk and compliance management systems that automate regulatory adherence, and threat intelligence applications that provide actionable insights on emerging adversarial tactics.
Deployment mode considerations influence adoption strategies, as cloud-based offerings deliver on-demand scalability and rapid feature updates, while on-premise deployments provide enhanced data sovereignty and predictable performance. Finally, the end user spectrum spans banking, financial services, and insurance institutions that demand high-volume transaction monitoring, energy and utilities providers focused on industrial control system security, government and defense agencies with stringent confidentiality requirements, healthcare organizations safeguarding patient records, IT and telecommunications firms managing expansive networks, manufacturing enterprises securing operational technology environments, and retail companies protecting both point-of-sale systems and e-commerce platforms. Enterprise size dynamics also play a role, with large organizations investing in end-to-end cognitive ecosystems, while small and medium-sized enterprises often opt for modular, service-driven models that minimize upfront capital commitments.
This comprehensive research report categorizes the Cognitive Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Security Type
- Technology
- Application
- Deployment Mode
- End User
- Enterprise Size
Evaluating Distinct Regional Dynamics Shaping Cognitive Security Evolution Across The Americas Europe Middle East Africa And Asia Pacific Markets
Across the Americas, cognitive security adoption is characterized by mature market dynamics and a robust vendor ecosystem. North American organizations prioritize integration capabilities and advanced analytics, driven by stringent regulatory mandates and high cybersecurity budgets. In contrast, Latin American enterprises focus on cost-effective service delivery and rapid deployment, leveraging managed cognitive security services to compensate for talent shortages and resource constraints. Transitions toward cloud-native cognitive solutions are accelerating throughout the region, supported by investments in digital infrastructure and growing partnerships between technology providers and regional system integrators.
In Europe, the Middle East, and Africa, regional insights reveal significant variation in adoption patterns. Western European countries emphasize data privacy and compliance, enforcing comprehensive security frameworks that incorporate cognitive analytics for real-time breach detection. Meanwhile, emerging markets in Eastern Europe, the Middle East, and Africa are increasingly exploring cognitive solutions to protect critical infrastructure, with energy and public sector organizations leading the way. Regional collaborations and industry consortia are fostering knowledge exchange, enabling stakeholders across disparate jurisdictions to establish standardized best practices and accelerate collective resilience against sophisticated threats.
Within the Asia-Pacific region, rapid digital transformation and expanding cloud ecosystems are driving widespread uptake of cognitive security technologies. East Asian markets such as China, Japan, and South Korea are at the forefront of AI research, integrating cognitive modules directly into network infrastructure for millisecond-scale threat response. Southeast Asian countries are likewise building regional security hubs, leveraging public-private partnerships to bolster regulatory frameworks and enhance cross-border threat intelligence sharing. Additionally, India’s burgeoning cybersecurity sector is focusing on indigenous cognitive solutions, supported by government initiatives aimed at nurturing homegrown technological capabilities and reducing dependency on imports.
This comprehensive research report examines key regions that drive the evolution of the Cognitive Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Leading Cognitive Security Vendors And Strategic Partnerships Driving Technological Innovations And Competitive Differentiation
Leading vendors in the cognitive security arena are distinguishing themselves through strategic alliances, proprietary research breakthroughs, and targeted acquisitions. Several established cybersecurity firms have embedded cognitive modules within their legacy platforms, enabling more sophisticated anomaly detection and automated response capabilities. These incumbents are complementing their core offerings by partnering with specialized AI startups to enrich behavioral analytics and natural language processing functions, thereby expanding their competitive moats.
Emerging pure-play cognitive security providers are carving out niches by focusing intensely on specific use cases, such as insider threat detection or fraud prevention. These companies prioritize modularity and flexibility, offering APIs and microservices that integrate across heterogeneous environments. Their agility in deploying updates and custom features has resonated strongly with mid-market customers seeking rapid time to value.
Strategic partnerships are also reshaping the ecosystem, as technology vendors collaborate with cloud hyperscalers to deliver integrated cognitive security services at scale. By co-developing cloud-native solutions, these alliances enable customers to benefit from global infrastructure footprints, elastic performance, and embedded threat intelligence feeds. Additionally, several prominent managed security service providers are enhancing their portfolios by incorporating cognitive analytics, delivering outcome-driven offerings such as continuous risk assessment and automated remediation services.
Investment trends further underscore the competitive landscape. Venture capital flows and corporate venture arms are funding AI-centric security startups, fueling research in advanced machine learning algorithms and next-generation threat hunting capabilities. Simultaneously, leading platform vendors are expanding R&D budgets to accelerate innovation cycles, ensuring that their cognitive security solutions remain at the cutting edge of effectiveness and usability.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cognitive Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Acalvio Technologies, Inc.
- Amazon Web Services, Inc.
- BlackBerry Limited
- Broadcom, Inc.
- Capgemini
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- CrowdStrike Holdings, Inc.
- CY4GATE SpA
- Cyberark Software Ltd.
- Darktrace Holdings Limited
- Deep Instinct Ltd.
- DXC Technology Company
- Feedzai
- FireEye, Inc.
- Fortinet, Inc.
- Google LLC by Alphabet Inc.
- Infosys Limited
- International Business Machines Corporation
- LexisNexis Risk Solutions by RELX
- LogRhythm, Inc.
- Mastercard Incorporated
- McAfee LLC
- Microsoft Corporation
- NEOM Company
- Nozomi Networks Inc.
- NVIDIA Corporation
- Okta, Inc.
- Oracle Corporation
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- RSA Security LLC
- Samsung Electronics Co., Ltd.
- SAP SE
- Securonix, Inc.
- SparkCognition, Inc.
- Tenable, Inc.
- Vectra AI, Inc.
Formulating Actionable Strategic Recommendations For Industry Leaders To Maximize Cognitive Security Efficacy And Achieve Sustainable Competitive Advantage
To harness the full potential of cognitive security, industry leaders should prioritize the integration of advanced analytics into existing security architectures. By embedding machine learning-driven detection engines at the network and endpoint layers, organizations can identify subtle threat indicators before they escalate into major incidents. Simultaneously, establishing cross-functional incident response teams that blend security analysts, data scientists, and IT operators will enable more effective interpretation of cognitive insights and faster remediation cycles.
Investment in talent and training is equally paramount. Security teams must develop proficiency in AI and behavioral analytics, understanding how to tune cognitive models and interpret probabilistic risk scores. Leaders should foster a culture of continuous learning, providing hands-on labs and simulation exercises that reinforce best practices. Additionally, partnering with academic institutions and industry research consortia can augment internal expertise and accelerate skill development.
Moreover, organizations should adopt a modular deployment strategy, piloting cognitive security solutions within high-risk domains such as financial transactions or industrial control systems before scaling enterprise-wide. This phased approach reduces operational disruption and allows teams to refine detection rules and workflows iteratively. Embracing cloud-based cognitive services can also minimize infrastructure overhead, enabling rapid scalability and streamlined feature updates.
Finally, proactive engagement with regulatory bodies and industry forums will ensure that cognitive security initiatives align with evolving compliance requirements. By transparently sharing threat intelligence data and participating in cross-sector information sharing, organizations can strengthen collective defense mechanisms and drive broader ecosystem resilience.
Outlining Rigorous Research Methodology Incorporating Multi Source Data Collection Industry Expert Consultations And Robust Analytical Frameworks
Our research methodology commenced with an exhaustive review of secondary sources, including industry white papers, academic journals, and public regulatory filings. This foundational intelligence established a baseline understanding of cognitive security technologies, market drivers, and competitive dynamics. Subsequently, we conducted in-depth interviews with a diverse array of stakeholders, including security architects, CIOs, regulatory experts, and solution providers, to capture real-world perspectives and validate emerging trends.
Quantitative data was aggregated through proprietary surveys targeting IT and security leaders across key verticals, ensuring representation from banking, healthcare, government, energy, and telecommunications. Responses were meticulously cleansed and normalized to facilitate comparative analysis. We employed a triangulation approach to corroborate insights, cross-referencing primary data with publicly available benchmarks and client case studies.
Analytical rigor was maintained through the application of established frameworks, such as SWOT for internal capability assessment, PESTLE for macroenvironmental analysis, and Porter’s Five Forces to evaluate competitive pressures. Additionally, our segmentation matrices were constructed via multivariate analysis, aligning component, deployment, security type, technology, application, deployment mode, end-user segments, and enterprise sizes to reveal nuanced market dynamics.
Finally, a dedicated editorial review panel evaluated all findings, ensuring methodological transparency, consistency of terminology, and alignment with industry best practices. This iterative validation process underpins the accuracy and reliability of our insights, equipping decision-makers with a robust foundation for strategic planning in the evolving cognitive security domain.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cognitive Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cognitive Security Market, by Component
- Cognitive Security Market, by Security Type
- Cognitive Security Market, by Technology
- Cognitive Security Market, by Application
- Cognitive Security Market, by Deployment Mode
- Cognitive Security Market, by End User
- Cognitive Security Market, by Enterprise Size
- Cognitive Security Market, by Region
- Cognitive Security Market, by Group
- Cognitive Security Market, by Country
- United States Cognitive Security Market
- China Cognitive Security Market
- Competitive Landscape
- List of Figures [Total: 19]
- List of Tables [Total: 1590 ]
Concluding Perspectives On Cognitive Security Trajectories Underscoring Strategic Imperatives And Emerging Opportunities For Stakeholder Empowerment
As the cyber threat landscape grows ever more complex, cognitive security stands at the vanguard of defensive innovation, offering organizations a dynamic, AI-powered shield against advanced adversaries. By synthesizing behavioral analytics, machine learning, and real-time threat intelligence, cognitive solutions empower security teams to anticipate attacks, reduce response times, and minimize business disruption. The convergence of these technologies is redefining best practices and setting new standards for proactive risk management.
Looking ahead, the ongoing evolution of adversarial AI and the proliferation of Internet of Things deployments will further underscore the importance of cognitive security. Organizations that invest in adaptable, data-driven defense frameworks will be best positioned to respond to emerging threats and regulatory shifts. Moreover, cross-industry collaboration and shared intelligence initiatives will play a pivotal role in fortifying collective resilience and accelerating innovation.
Ultimately, cognitive security is more than a technological upgrade-it represents a strategic imperative for enterprises seeking to safeguard their digital assets and maintain stakeholder trust. By embracing these next-generation defense mechanisms, decision-makers can turn cybersecurity from a defensive cost center into a catalyst for operational excellence and competitive differentiation.
Unlock Comprehensive Cognitive Security Insights And Accelerate Your Cyber Defense Strategy By Engaging With Ketan Rohom Today
Are you prepared to elevate your organization’s defense posture with cutting-edge cognitive security intelligence? Reach out directly to Ketan Rohom, Associate Director of Sales & Marketing, to gain firsthand access to our comprehensive market research report. By engaging with Ketan Rohom, you unlock a personalized consultation designed to align our insights with your unique business challenges and strategic ambitions.
Through this tailored interaction, you will benefit from expert guidance on integrating cognitive security solutions that drive operational efficiency and fortify threat resilience. Ketan Rohom will walk you through the report’s key findings, demonstrating how these insights can translate into actionable initiatives that deliver measurable ROI. This exclusive opportunity ensures that your investment in cognitive security aligns with emerging market dynamics and industry best practices.
Don’t miss the chance to secure a competitive edge in the face of evolving cyber threats. Schedule your consultation with Ketan Rohom today and initiate a transformative journey toward proactive risk management and sustained innovation. Contact him now to obtain the full market research report and position your organization at the forefront of cognitive security excellence.

- How big is the Cognitive Security Market?
- What is the Cognitive Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




